Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

Many Facebook users may not even realize that their private phone number is connected to their Facebook account, having forgotten that they did so. Facebook isn't allowed to simply extract your number from your phone, but they can do what I refer to as the "app equivalent of cyberbullying" by repeatedly asking you to confirm and save your number each time you launch Facebook.
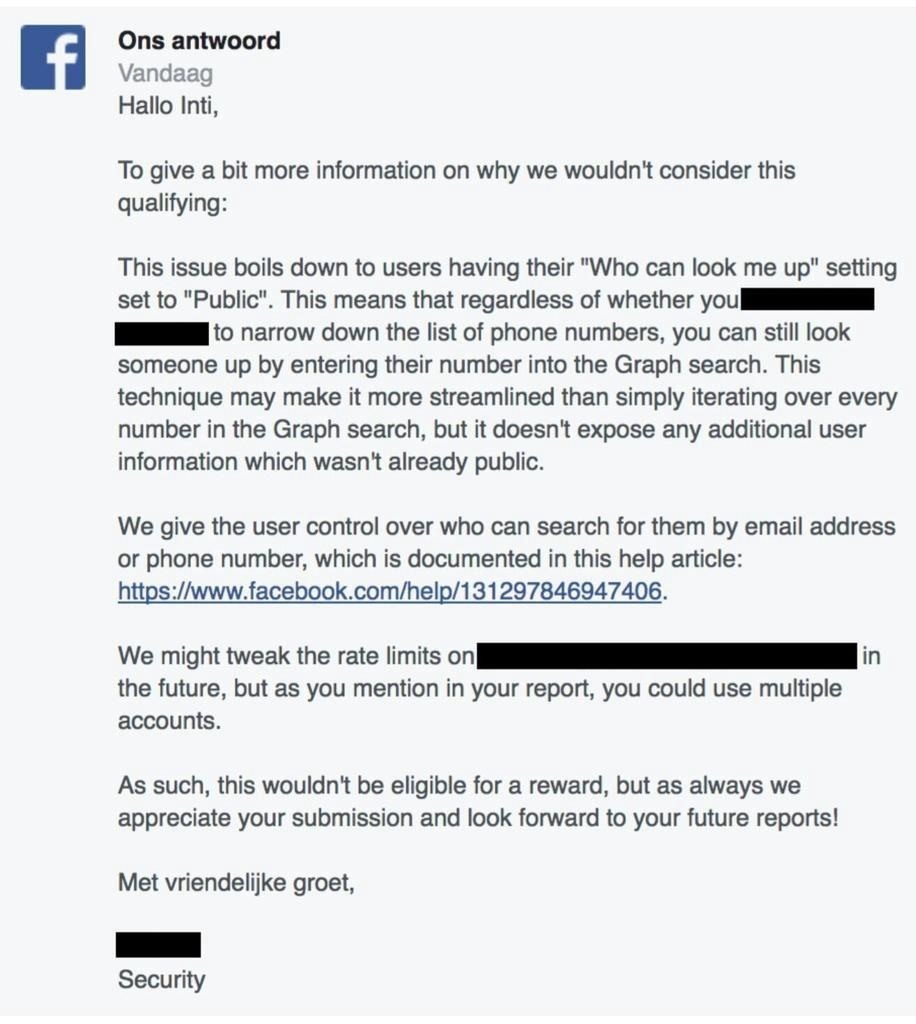
The default privacy setting on Facebook allows anyone to search for you by your phone number once you add it. This is not a new issue. It has been around as long as the Facebook Graph search, but Facebook chooses to see this issue as a feature, as a letter received by Belgian researcher Inti De Ceukelaire shows.
Certainly, some people, such as celebrities and politicians, should be more concerned than others about revealing their private number online. However, anyone could potentially have a cyberstalker or hacker target them. Once a hacker has a phone number and your name, they can quickly use open-source intelligence (OSINT) tools that has been covered on Null Byte to grab further public data like occupation, employer, spouse, relationship, any other public info.
A hacker could use the information to further social-engineering attacks by calling you directly. Think of the classic " Microsoft tech support" scam, only the caller trying to trick you knows your name and intimate details of your personal life. Armed with these, it's easy to make the target think the caller is legitimate.
How would a hacker actually go about finding your number? In theory, if they had a lot of time, they could just search all 9,999,999,999 potential numbers until they stumbled upon yours. Clearly, this isn't very efficient, so let's see the right way of doing it. For a practice subject, I'll be using DC Mayor Muriel Bowser (2017) as a random city official. In the examples below, her number was changed to protect her real number.
A hacker could use the information to further social-engineering attacks by calling you directly. Think of the classic " Microsoft tech support" scam, only the caller trying to trick you knows your name and intimate details of your personal life. Armed with these, it's easy to make the target think the caller is legitimate.
How would a hacker actually go about finding your number? In theory, if they had a lot of time, they could just search all 9,999,999,999 potential numbers until they stumbled upon yours. Clearly, this isn't very efficient, so let's see the right way of doing it. For a practice subject, I'll be using DC Mayor Muriel Bowser (2017) as a random city official. In the examples below, her number was changed to protect her real number.
Step 1. Use the Area Code
If you think of a target's phone number as one of all the possible 10-digit US phone numbers, you can quickly see that 10 billion North American phone numbers it far too large a list to effectively search through. Luckily for the hacker, he can cut this down thanks to the North American Numbering Plan (NANP) which lays out the guidelines for phone numbers in the US.
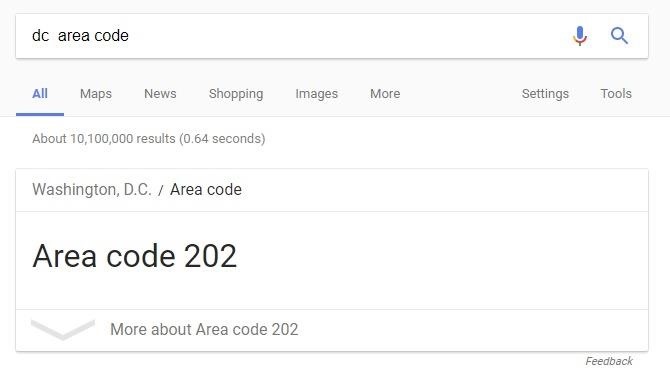
Let's take an example: 234-235-5678. Looking at the NANP, we can see that the first three numbers (234) are the area code, and the plan allows for 2–9 as the first digit and 0-9 for the second and third digits. That information right there eliminates one billion possible numbers from the hacker's list.
The hacker can also quickly take advantage of this if they know or can take an educated guess at where you live, as it's as easy a Google search. By doing this, the hacker can remove a further 9 billion 990 million numbers from the list of potential guesses.
The next three numbers after the area code in our example (235) are the central office prefix. Again, the plan calls for 2–9 for the first digit and 0–9 for both the second and third digits, but with a caveat.
In area codes where the second digit is 1, the third can't also be 1. This yet again removes a large number of phone numbers from the hacker's list. The last four digits of the phone number is the line number, in this case, 5678.
I took the educated guess that the Mayor of DC would have a DC area code, and a hacker could also look up the target's Facebook account and likely find a hometown or the current city the target lives in or works from. Some larger cities like Los Angeles will have multiple area codes within them, but no matter how many "split" area codes there are, it still greatly reduces the hacker's list of possible numbers.
Step 2 Get the Last Numbers
Now that I know my target's number is 202-???-????, I want to try and remove as many of those question marks as possible, making it easier to do a Facebook search later on. Thankfully, Facebook has our back and has made this probably the second easiest step, after using the area code. In order to get the last two numbers, we just have to go a few steps into the password reset process.
To do this, the hacker goes to the main Facebook page and clicks "Forgot account" to start the process.
Next, they enter the target's name they have in mind and click the "Search" button.
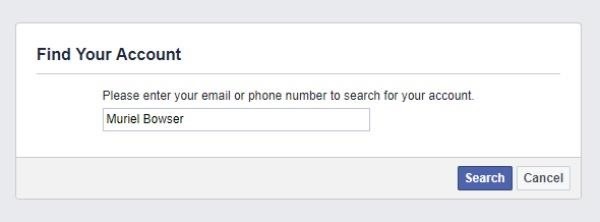
The hacker is then presented with a list that includes a face picture paired with each matching account that helps them quickly identify their target. There's our target right at the top!
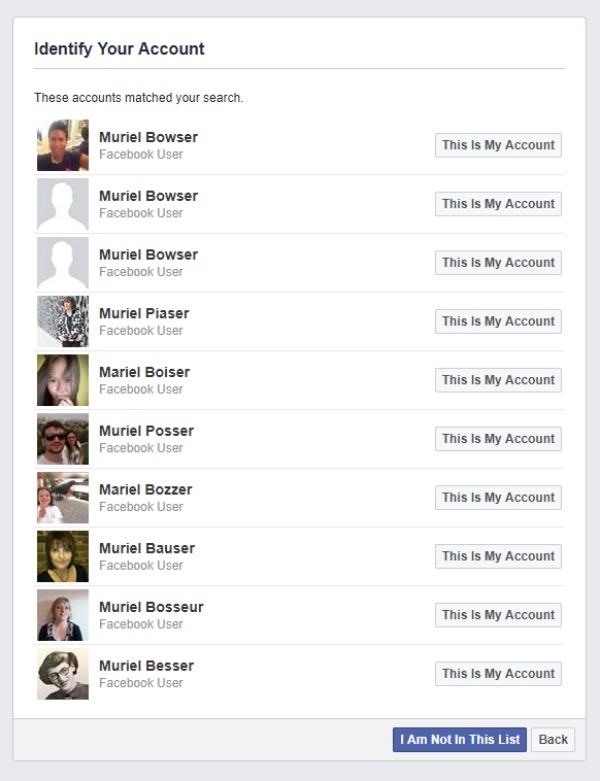
Facebook then kindly provides the hacker the last two digits of the targets number, along with some information about the emails accounts associated with their Facebook account, such as the first and last letter, and sometimes the email domain.
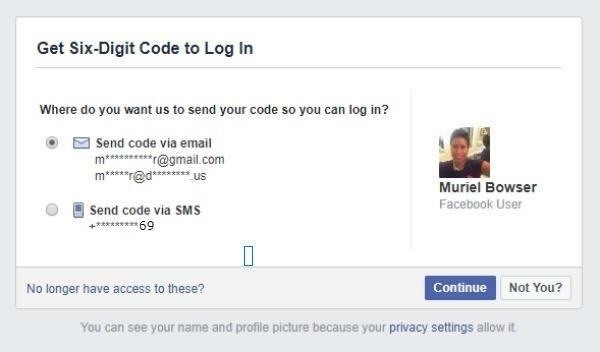
That's as far as the hacker has to go. They don't actually reset the password, and they shouldn't so that the target never receives any kind of notification to tip them off.
Step 3 Use Outside Sources
With over 218 million users, PayPal and other services can help add to the information the attacker has collected so far. In this case, if the target is a PayPal user, the hacker can get two additional digits of the phone number we're looking for.
In the picture above, you may have noticed that the first email listed is a Gmail account that starts with "M" and ends with "R."
That's funny, since my targets first name starts with an "M," and her last name ends with an "R." To a hacker, this screams "I used my name as my email!" Suspecting this was the case, I checked it on Gmail by typing it in.
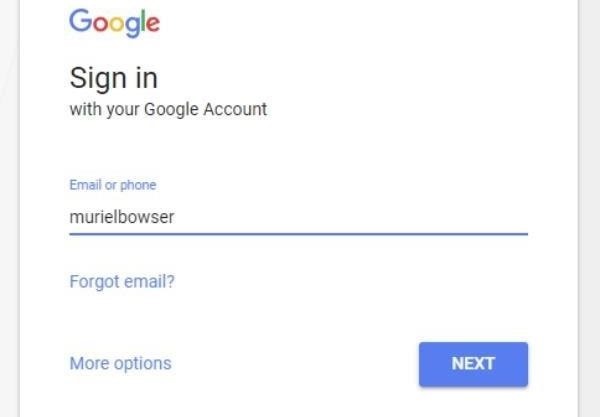
Google accepted it, but that doesn't necessarily mean that it's the target's email. The hacker can check by doing the same password reset trick they pulled with Facebook.
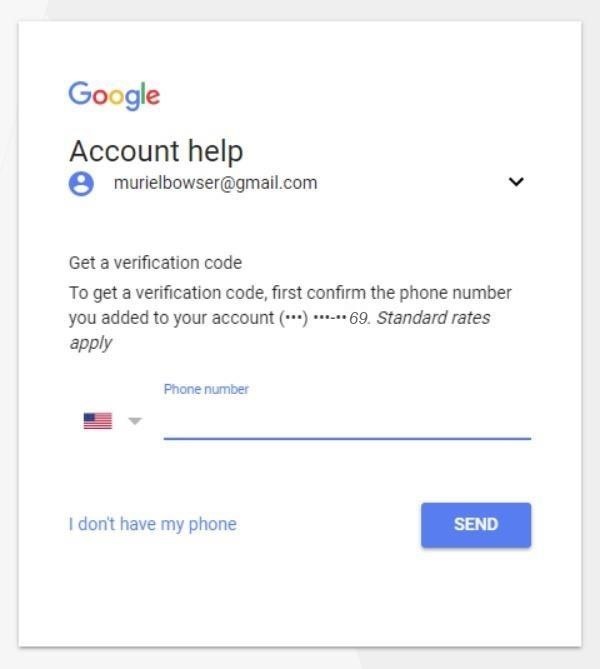
Yep, this account just so happens to have a number that ends in 69. Coincidence? I think not. Now that I have an email to work with, I can jump over to PayPal in a new tab, and once again, use the same password reset trick.
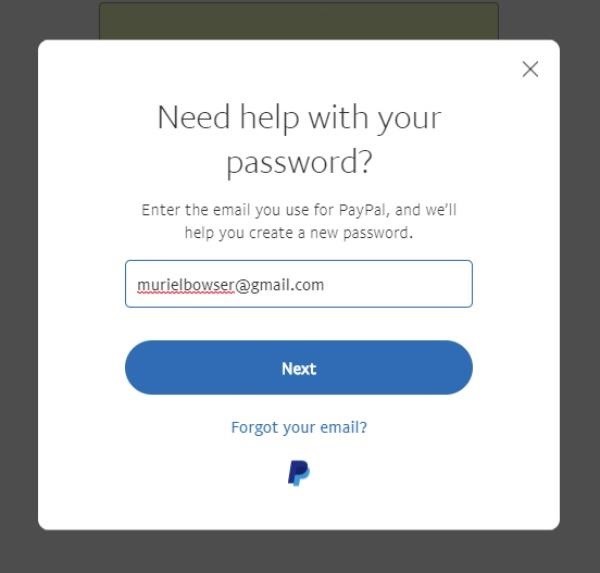
This time, when I get to the password reset screen, I get not only all four digits of the line number, but also the first number of the area code too!
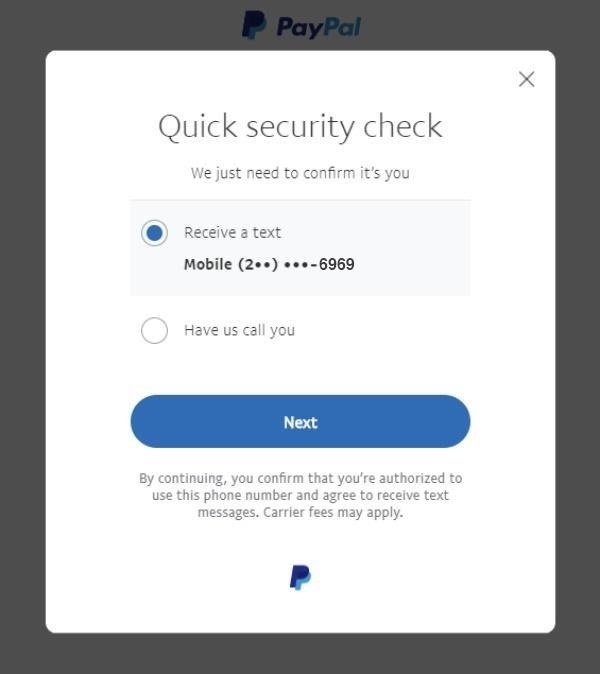
This allows me to be reasonably sure that I'm on the right track with the area code, and verifies my previous work on finding the last few numbers. This means I have the number 202-???-6969 so far. In other words, my list has gone from 10 billion choices to about a thousand in just a few minutes of work.
Step 4Brute-Force It the Smart Way
At this point, a hacker could just start throwing numbers into the Facebook search bar, but that still wouldn't be that efficient. So what does a lazy hacker do? They take advantage of a Facebook feature that allows you to conduct a bracket search.
Facebook allows you to upload lists of contacts in CSV format, and then tells you if they are on Facebook so you can add them as friends. By constructing my own contact list of potential numbers, I can quickly rule out large chunks of wrong numbers.
In this case, I know the number has to be in the range from 202-000-6969 to 202-999-6969. By cutting that in half and creating a list of numbers from 202-000-6969 to 202-500-6969, I can effectively rule out half of my list, as the target will only be in one of the two half lists created. Then, I can upload the list and instantly determine if they are on it or not.
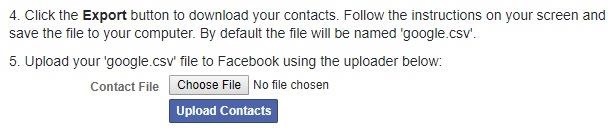
To create this list, I went to Google Contacts and clicked "Export" to get a sample CSV file to work from.
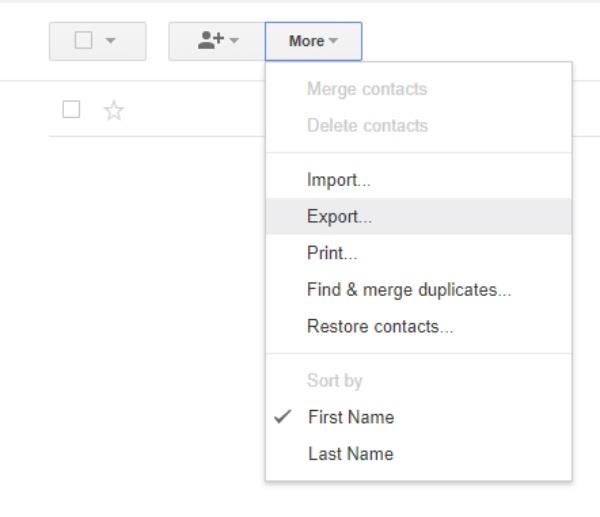
Facebook prefers to accept the list in Google CSV format, so I saved it as such from Google Contacts.
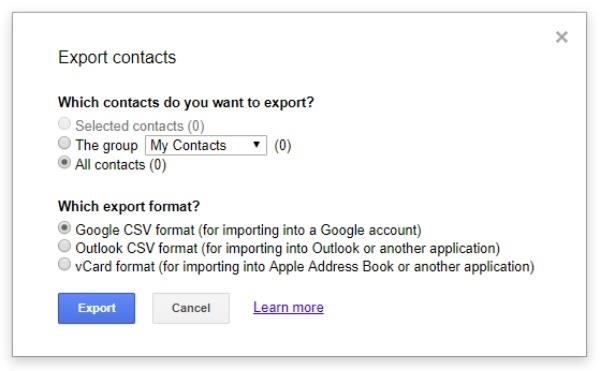
From there, a hacker can open the file in Google Sheets or Excel and change the column formula for the phone numbers to one that will iterate over the numbers they need to check, as seen in the following example.
In the excel formula below, I start by taking the lowest value phone number, in this case, 2020006969, then I add 10,000 to it in order to increase the fifth place digit by 1. This formula will repeat as many times as needed, but we shouldn't do it more than 1,000 times because there are only a thousand numbers in our list to guess. If the target hadn't had a PayPal account to help us derive the third and fourth place digit, then we would be adding 100 to increase the third digit instead.
=(ROW()*10000) +2020006969
From there, it is simple to sign into a Facebook account and go to the Friend Finder feature. Click on the Gmail logo and then "Find Friends."
Next, scroll to the bottom of the page and upload your CSV file containing the phone numbers you wish to try.
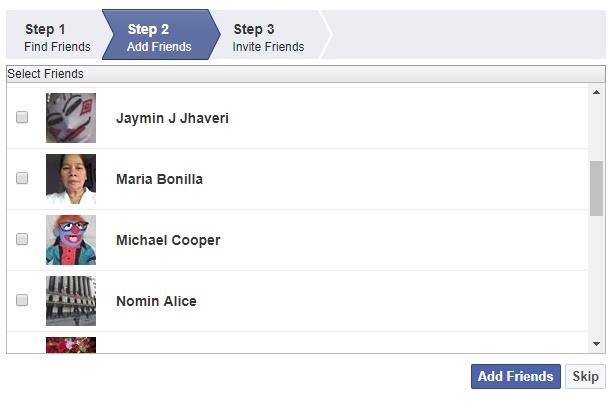
After it's uploaded, Facebook presents the hacker a list of "Friends" to add from the list. They would then search for their target inside that list. My target doesn't seem to be here, so I know they aren't in this half of our batch of numbers.
Next, instead of testing the next 500, I split the next 500 in half and check one of those halves. This is because I already know the target will be on the second list since they weren't in the first half. The hacker can continue searching in this way until the target appears on a phone number list.
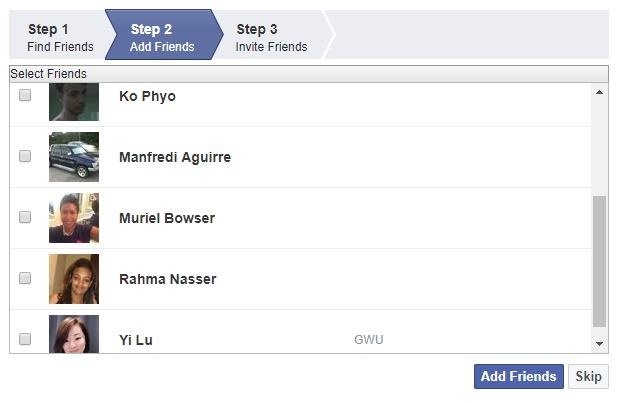
From there on out, the hacker would test smaller and smaller batches of numbers until they have only a handful to test. I stopped when I had it down to about 30 numbers. Obviously, this will take longer if the hacker has less information about the other digits of the phone number to begin with, as they will have a larger number set to search. Facebook will rate-limit the hacker to five attempts per day but they can get around this by signing into another account.
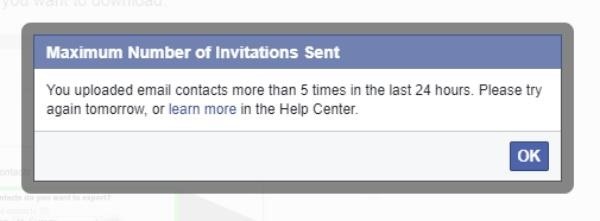
Step 5 Test the Last Few Numbers
Once that hacker has it down to a handful of numbers, they can go to the Facebook search bar and type them in one by one. To do so, just type the number into the search bar with no hyphens. If the requests are going too fast, or if they search for too many, Facebook starts to rate-limit them with a CAPTCHA.
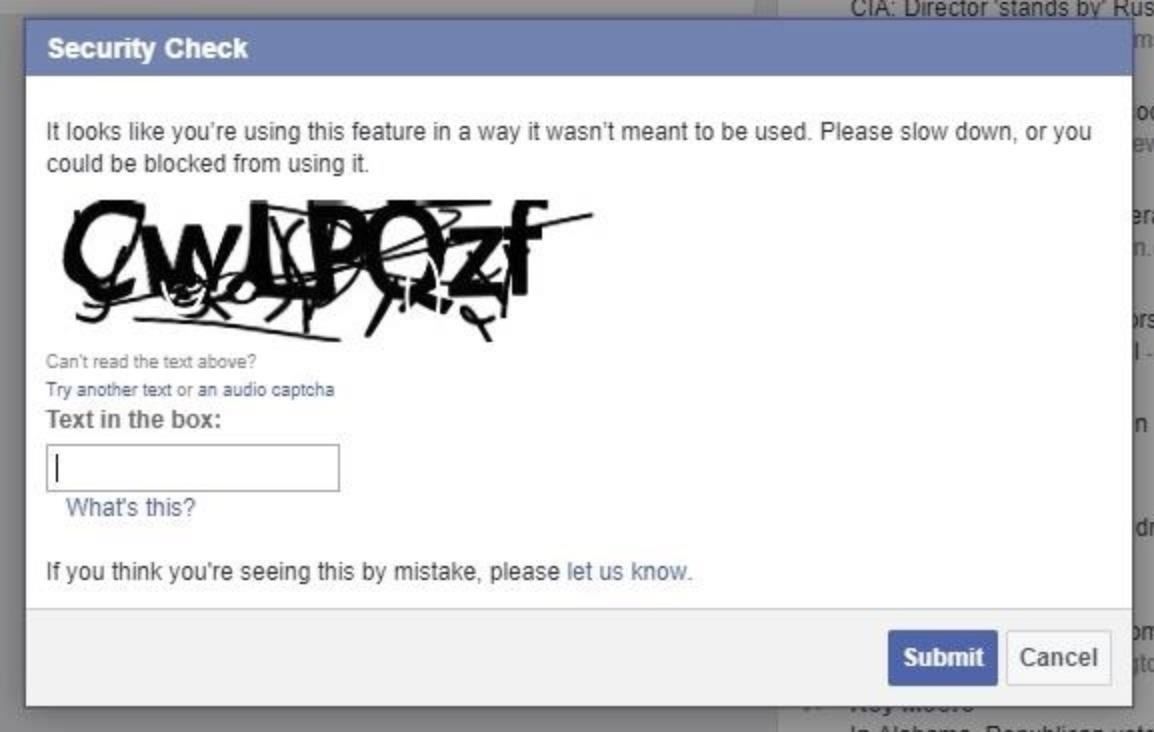
However, that's not much of a defense when the hacker only has 30 numbers to check.
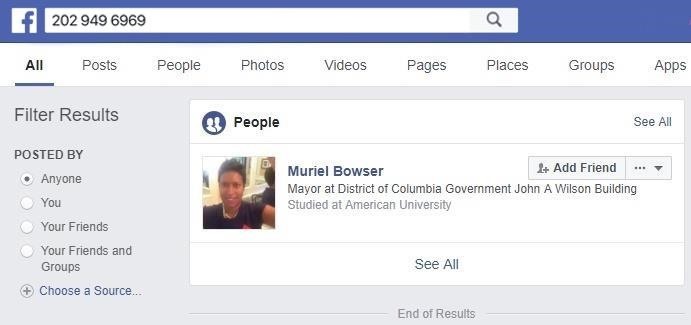
In total, it took me around 30 minutes to an hour to find the target's number, and these same steps could be used on anyone who has their phone connected to Facebook.
Step 6 Protect Yourself
The simplest way to protect yourself is to never connect your phone to Facebook. If you still want to use two-factor authentication, Facebook allows you to use a USB U2F device without having to rely on your phone.
If you absolutely must have your phone connected, navigate to Facebook Settings, select "Privacy," then "Who can look you up using the phone number you provided?" Set this option to "Friends." Unfortunately, Facebook doesn't let you set this to "Only me."
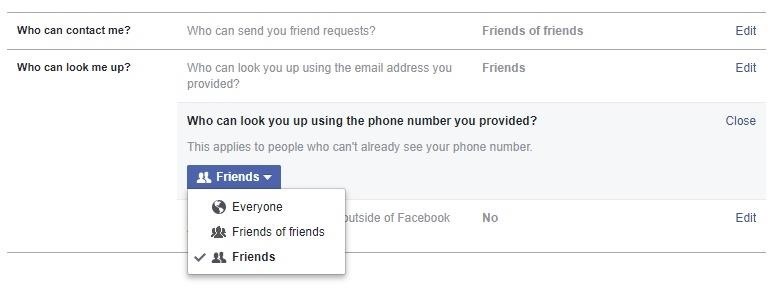
On a mobile device, you would tap on the three-line menu icon, select "Account Settings" (iOS users will have to select "Settings" first), then tap on "Privacy." You'll see the same "Who can look you up" question above where you can change your preferences to "Friends" only.
While this still will not provide absolute protection, it will make the hacker's life much more difficult.
Thanks for reading! If you have any questions, you can leave a comment here.

إرسال تعليق